Singapore- SingHealthhttps://www.zdnet.com/article/employees-sacked-ceo-fined-in-singhealth-security-breach/
Exploit: Initial malware infection coupled with a multi-pronged attack.SingHealth: Singapore’s largest group of healthcare institutions.
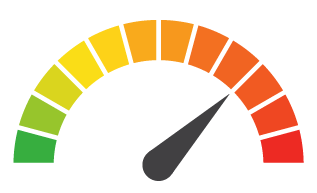 | Risk to Small Business: 1.444 = Extreme: Besides for the relentless onslaught of articles and news detailing SingHealth’s negligence and lack of “security hygiene”, high-profile members of management were terminated, demoted, and fined. As you can imagine, the long-term implications for employee morale are less than desirable, along with crippling blows to culture, brand, and customer trust. |
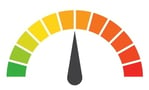 | Individual Risk: 2 = Severe: Although the theft initially occurred between a short period of time (June 27, 2018 to July 4, 2018), data stolen included names, NRIC numbers, addresses, gender, race, and dates of birth. Even worse, around 160,000 also had their outpatient prescriptions taken. It is believed that Prime Minister Lee Hsien Loong was a primary target for the hack, but you can expect the data collected to be sold to the highest bidder. |
Customers Impacted: 1.5M individuals.How it Could Affect Your Customers’ Business: Aside from the laundry list of penalties for incurring such a breach, an affected organization must continue business as-is while restoring operations. In this case, SingHealth has imposed a “temporary Internet surfing separation” on 28,000 staff’s work computers. With an entirely new set of security processes to manage while avoiding disruptions caused by the breach, customers should begin to see the value in proactively implementing IT protocols and monitoring for stolen credentials.ID Agent to the Rescue: SpotLight ID allows MSPs, Resellers and Channel Partners to deliver comprehensive personal identity protection for clients’ employees and customers, ultimately safeguarding corporate systems. Get started here: https://www.idagent.com/identity-monitoring-programs.
Risk Levels:1 - 1.5 = Extreme Risk1.51 - 2.49 = Severe Risk2.5 - 3 = Moderate Risk*The risk score is calculated using a formula that considers a wide range of factors related to the assessed breach.




No comments:
Post a Comment