Australia- First Nationalhttps://www.zdnet.com/article/finger-pointed-at-real-estate-recruiter-after-australian-cv-leak/
Exploit: Leak by “third-party” recruitment agency, Sales Inventory Profile.First National: Real estate network.
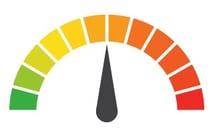 | Risk to Small Business: 2 = Severe: Gareth Llewellyn, a security researcher at Brass Horn Communications, originally discovered how the CVs of job applicants of First National had been “inadvertently published” online. At least 12 company offices were affected, and the breach has been pinned to a third-party vendor, Sales Inventory Profile. Such a breach can negatively impact the brand reputation of the organization, even though the vulnerability came from a recruiting agency. Yet another example of why it is crucial to evaluate third-party vendors and secure data on all fronts. |
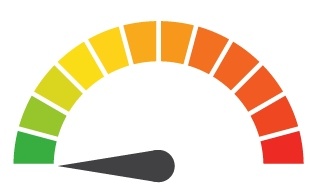 | Individual Risk: 2.571 = Moderate: Published CV’s included full names, addresses, phone numbers, date of births, and other personal information. Even without payment information, customers should be weary of unusual transactions. |
Customers Impacted: 2,000 job applications.How it Could Affect Your Customers’ Business: Small breaches that expose personal details have consequences that are not easily quantified monetarily but can be catastrophic. Promising employees could choose to work elsewhere, whether or not a third-party was liable for the breach. Businesses must increase the importance they place on database and vendor management in order to protect user privacy and safety.ID Agent to the Rescue: See why Peter Verlezza, Managing Director at SMB Networks uses Dark Web ID and SpotLight ID to monitor real-time domain and login credentials: “I’m already helping to protect my customers with real-time domain monitoring provided by Dark Web ID. By protecting the people who work for those customers with the affordable and government-tested personal identity monitoring SpotLight ID delivers, I know my customer’s business is that much safer from potential breach”.
Risk Levels:1 - 1.5 = Extreme Risk1.51 - 2.49 = Severe Risk2.5 - 3 = Moderate Risk
*The risk score is calculated using a formula that considers a wide range of factors related to the assessed breach.




No comments:
Post a Comment