Bit by bit helps client networks run smooth and secure.. visit our website at www.bitxbit.com/texas 877.860.5863
Technology companies come and go, but Bit by Bit backs its service with 30 years of experience helping businesses achieve their goals with reliable IT solutions and support. We were established in 1987 as a database application development and networking company, and since then we’ve evolved into a full-service IT firm and leader in delivering powerful and cost-effective technology solutions. visit our site at www.bitxbit.com
Saturday, January 30, 2021
Dropbox Scam
Bit by bit helps client networks run smooth and secure.. visit our website at www.bitxbit.com/texas 877.860.5863
Thursday, January 28, 2021
Another Password expiring scam:
Bit by bit helps client networks run smooth and secure.. visit our website at www.bitxbit.com/texas 877.860.5863
How Strong is the Lock on the Door to Your Data?
You wouldn’t trust a flimsy old lock to secure the door to your business. Why are you trusting one to secure your business systems and data? It sounds logical that you’d want the most secure lock on your office door, but many companies don’t extend that logic to the access points to their systems and data, leaving them wide open to cybercriminal mischief.
In a recent survey, only 24% of businesses were using security access controls, like a secure identity and access management solution instead of old-fashioned password-based security. That’s a boon for cybercriminals – compromised passwords are the key to entry for them in around 85% of all data breaches. Strong access point security isn’t just something for major corporations anymore. Every business needs it, and solutions like Passly ensure that every business can afford it.

Would you trust a flimsy lock for your front door? Add a stronger lock between cybercriminals and your business when you learn to Build Better Passwords. GET IT>>
Protecting your systems and data with just a password isn’t going to cut it anymore. Even if your employees are making good, complex passwords and practicing excellent password hygiene, relying on passwords alone is outmoded and dangerous. Huge stores of passwords that have been stolen in past data breaches are available in Dark Web markets and data dumps to power credential stuffing attacks and other cybercrime.
Passly makes it easy and affordable to defend against password-based attacks with the tools that experts recommend: multifactor authentication, single sign-on, secure shared password vaults and more. Plus, Passly deploys in days, not weeks for an immediate security improvement. Don’t wait to beef up your access point security. Add a secure identity and access management solution today and make sure that the access points to your systems and data are really protected.
Need help give us a call, 877.860.5863 x190
Office 365 Scam - Password Expires today
Friday, January 22, 2021
Do you think this is a scam?? Why or why not?
Thursday, January 21, 2021
Be careful.. more scams everyday..
Bit by bit helps client networks run smooth and secure.. visit our website at www.bitxbit.com/texas 877.860.5863
Wednesday, January 20, 2021
Can Your Staff Really Spot Phishing Messages? Can You?
Can Your Staff Really Spot Phishing Messages? Can You?
Phishing is a threat that looms large for every business. In 2020, phishing threats grew by more than 600% as cybercriminals took advantage of a perfect storm of factors that gave them great advantages: a newly remote workforce, world unrest, the COVID-19 pandemic and a crashing economy.
That’s definitely a growth category for cybercrime in 2021. Damage related to cybercrime including phishing-related threats like ransomware and business email compromise is projected to hit $6 trillion annually in 2021 as a new cyberattack is launched every 39 seconds.
One of the best investments that you can make to protect your business from today’s worst cyberattack threats is security awareness training featuring phishing resistance. We’re making that easier than ever before with the newly updated BullPhish ID.
Featuring user-friendly training portals, customizable training materials, and simple remote management, BullPhish ID is the top-flight training solution that includes everything that you need to get your team ready to face down phishing at an excellent price.
Don’t wait to start your 2021 security awareness and phishing resistance training program. Act now to start protecting your business from cybercrime before one click on one phishing email costs you a fortune.
Bit by bit has security packages that can help secure your network, call today to schedule a time to learn more about how we can help.
Top Threats this week
Top Compromise Type: Domain
Top Industry: Health & Medical Research
Top Employee Count: 501+
Friday, January 15, 2021
Don't fall for the dropbox invoice SCAM
Thursday, January 14, 2021
Don’t Let Employee Blind Spots Cost You a Fortune
Don’t Let Employee Blind Spots Cost You a Fortune
The number one cause of a data breach never changes – it’s always human error. No matter how savvy you may think your staffers are about cybersecurity, everyone has a blind spot. How can you find your employees’ blind spots and make sure that you’re covering all of your bases?
A recent report called Cyberchology: The Human Element details some of the unfortunate consequences that the sudden shift to remote work and the stress of the pandemic has brought to the table. The most striking observation? Just over 80% of companies experienced cybersecurity challenges due to human error in 2020.
While human error is always going to the top cause of a data breach or similar cybersecurity incident, you can take steps to reduce that possibility by creating an atmosphere for your employees that makes it okay, or even encouraged, to ask questions and learn more about cybersecurity. A well-informed, confident staff is your secret weapon against cybercrime.
A strong cybersecurity culture is rooted in accessible, up-to-date, easy to understand security awareness training that includes phishing resistance. It’s important to use tools like training with BullPhish ID as exercises that nourish your healthy cybersecurity culture, not punishments to be endured. That’s why we’re careful to include memorable, animated video lessons in our training content menu.
Making training pleasant and manageable for even your most tech-shy staffer helps foster a spirit of teamwork that has your staffers watching out for trouble to make sure that those blind spots are covered – because when every staffer is trained to spot and stop cybersecurity threats, everyone in your organization is on your defense team.
Wednesday, January 6, 2021
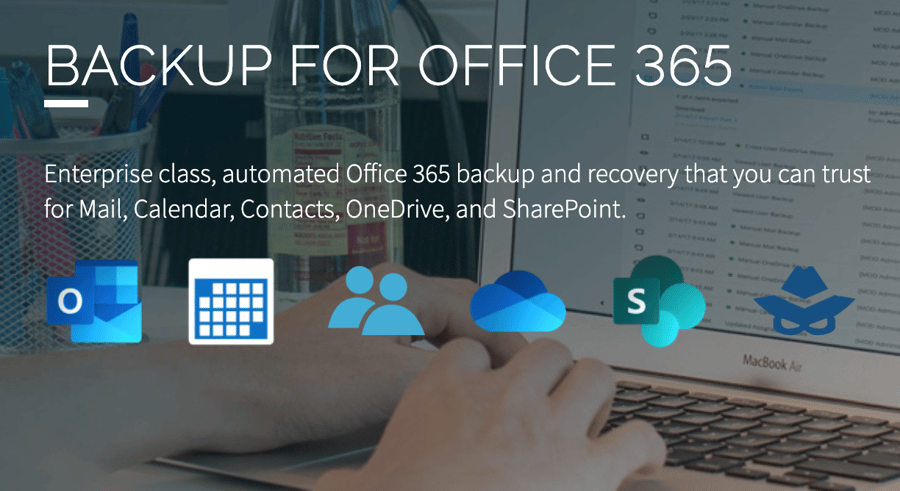
Why & How to Back Up Your Office 365
Presented by |
 |
Did you know your organization could be losing Office 365 data every day?
Yes, every day.
It's the accidental activity, user errors, ransomware, data corruption, and deletions that put you at risk. Yet, you own your data and it's your responsibility when you make a mistake — or when a malicious act stops your business cold. Then what?
Join us for this important 30-minute webinar where you’ll learn why and how Spanning will safeguard your data with its powerful, yet easy-to-use cloud-to-cloud backup and recovery solution.
You will learn:
|
Can't Get Enough of Spanning?You're in luck. Join us for our next webinar: Salesforce Automated Backup & Restore Tuesday, February 23, 2021 1:00 - 1:30 p.m. EST |
About Our Presenter |
Dave WallenDirector, Product MarketingSpanning
Dave Wallen is a veteran industry evangelist with a passion for promoting innovative cloud solutions that help organizations improve performance and maximize their return on investment. As Director of Product Marketing for Spanning, he’s focused on industry and market research, customer insight, go-to-market planning and spreading the word about Spanning’s solutions for Office 365, G-Suite, and Salesforce. |
 |
-
Bit by bit helps client networks run smooth and secure.. visit our website at www.bitxbit.com/texas 877.860.5831
-
What is SOC-as-a-Service? By Robert Blake Having a Security Operations Center (SOC) in-house is expensive for the average business. Large ...
-
In today's digital age, where the internet is an integral part of our lives, safeguarding our digital devices from malicious threats is ...