United States - Partners in Carehttp://kbnd.com/kbnd-news/local-news-feed/438344
Exploit: Phishing attackPartners in Care: Healthcare provider based in Bend, Oregon
Exploit: Phishing attackPartners in Care: Healthcare provider based in Bend, Oregon
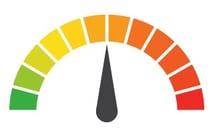 | Risk to Small Business: 1.777 = Severe: A phishing attack compromised an employee’s email account towards the end of 2018, providing hackers with access to patients’ health information between November 17 and December 12. After completing a manual email review, the company concluded that sensitive patient information was exposed during the breach. |
 |
Individual Risk: 2 = Severe: Although it is unclear how many records were compromised in the breach, hackers were able to access patients’ personal information including names, birth dates, medical records, and social security numbers. Patient records related to diagnosis, medications, and insurance details were also revealed. The organization notified those impacted by the breach and are encouraging them to monitor their account statements for suspicious activity.
|
Customers Impacted: Unknown
How it Could Affect Your Customers’ Business: Companies managing sensitive healthcare information are expected to have mechanisms in place to protect their patients, so a preventable data breach is particularly egregious. While phishing scams are used to gain access to a company’s IT infrastructure, they can be prevented through training and monitoring tools.
ID Agent to the Rescue: BullPhish ID™ simulates phishing attacks and conducts security awareness training campaigns to educate your employees, making them the best defense against cybercrime. Click the link to get started: https://www.idagent.com/bullphish-id.
How it Could Affect Your Customers’ Business: Companies managing sensitive healthcare information are expected to have mechanisms in place to protect their patients, so a preventable data breach is particularly egregious. While phishing scams are used to gain access to a company’s IT infrastructure, they can be prevented through training and monitoring tools.
ID Agent to the Rescue: BullPhish ID™ simulates phishing attacks and conducts security awareness training campaigns to educate your employees, making them the best defense against cybercrime. Click the link to get started: https://www.idagent.com/bullphish-id.
Risk Levels:1 - 1.5 = Extreme Risk1.51 - 2.49 = Severe Risk2.5 - 3 = Moderate Risk*The risk score is calculated using a formula that considers a wide range of factors related to the assessed breach.
United States - Citrixhttps://www.bleepingcomputer.com/news/security/citrix-confirms-hackers-stole-sensitive-employee-personal-information/
Exploit: Password spraying
Citrix: Multinational software company providing application and software services
 | Risk to Small Business: 2.333 = Severe: Hackers took advantage of weak employee passwords and gained entrance to the company’s network via password spraying. Once inside, they were able to access internal documents and information on former and current employees for about six months. The bad actors were expelled from the network, and the company took measures to improve the company’s password security. |
 | Individual Risk: 2.248 = Severe As part of an ongoing investigation, it was revealed that financial information and social security numbers of employees were at risk, in addition to internal business assets. Even worse, the company also disclosed that hackers were able to view personal information of employees’ beneficiaries and dependents. Current and former employees are encouraged to sign up for identity protection services to monitor their credentials. |
How it Could Affect Your Customers’ Business: Recovering from a data breach that not only compromises employee information but also that of their dependents and beneficiaries can be an arduous process. Employees lose trust and goodwill in their employer, and it becomes difficult for them to discern the long-term consequences once personal data is accessed. Therefore, proactively providing identity monitoring services can go a long way in demonstrating a commitment to employees while mitigating security risks for the company as a whole.
ID Agent to the Rescue: SpotLight ID™ allows MSPs, Resellers and Channel Partners to deliver comprehensive personal identity protection for clients’ employees and customers, ultimately safeguarding corporate systems. Get started here: https://www.idagent.com/identity-monitoring-programs
Risk Levels:1 - 1.5 = Extreme Risk1.51 - 2.49 = Severe Risk2.5 - 3 = Moderate Risk
*The risk score is calculated using a formula that considers a wide range of factors related to the assessed breach.United States - Microsofthttps://www.bleepingcomputer.com/news/security/office-365-accounts-compromised-via-ato-attacks-used-in-bec-scams/
Exploit: Account takeover attack
Microsoft: Multinational technology company based in Redmond, Washington
Microsoft: Multinational technology company based in Redmond, Washington
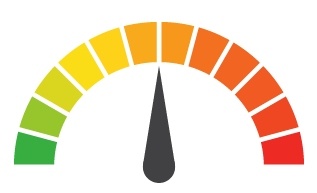 | Risk to Small Business: 2.111 = Severe: Hackers used many different maneuvers including brand impersonation, social engineering, and phishing scams to gain access to the email accounts of Office 365 users. Once inside, the cybercriminals implemented a variety of inbox rules to hide their behavior as they sent thousands of emails intended to facilitate spear phishing, BEC attacks, and malvertising campaigns. |
 | Individual Risk: 2.284 = Severe: While hackers gained access to user email accounts, it appears that their primary purpose was to proliferate the scam by sending emails to unsuspecting recipients. However, users with compromised Office 365 accounts should immediately change their passwords while also being mindful of the potential for data misuse. |
How it Could Affect Your Customers’ Business: Email account compromises are the center of many data breaches today, and it’s time that small businesses take notice. The good news is, securing employee and user accounts can be achieved by partnering up with the right cybersecurity training solution.
ID Agent to the Rescue: With BullPhish ID™, MSPs can provide a more complete picture of a company’s security posture and potential risk, transforming the weakest links of an organization into their strongest points of protection. Find out how you can get started with us here: https://www.idagent.com/bullphish-id
Risk Levels:1 - 1.5 = Extreme Risk1.51 - 2.49 = Severe Risk2.5 - 3 = Moderate Risk*The risk score is calculated using a formula that considers a wide range of factors related to the assessed breach
United States - Docker Hubhttps://www.cshub.com/attacks/articles/incident-of-the-week-impact-of-docker-security-breach
Exploit: Unauthorized databass access Docker Hub: Online platform for procuring container applications
 | Risk to Small Business: 1.777 = Severe: When an unauthorized third party breached Docker Hub’s database, they gained access to sensitive data including usernames, passwords, and other account features. Although the company immediately notified users of the attack, the hackers gained extensive system access, ultimately compromising nearly 200,000 accounts. Even worse, it’s possible that the software applications that users built on the platform could be impacted by the breach. |
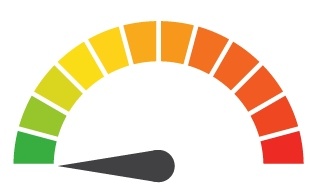 | Individual Risk: 2.571 = Moderate: The organization insists that financial information was not accessed during the breach, but hackers did gain extensive information about Docker Hub customers. Anyone with a Docker Hub account should enroll in identity and financial monitoring services. |
How it Could Affect Your Customers’ Business: Docker Hub is being scrutinized for avoiding the implementation of industry’s security best practices, such as two-factor authentication, which could have allowed them protect users from this breach. Small businesses operating in the B2B space need to ensure that they are doing everything possible to protect customer data by partnering up with MSPs with state-of-the-art cybersecurity technology.
ID Agent to the Rescue: SpotLight ID allows MSPs, Resellers and Channel Partners to deliver comprehensive personal identity protection for clients’ employees and customers, ultimately safeguarding corporate systems. Get started here: https://www.idagent.com/identity-monitoring-programs.
Risk Levels:1 - 1.5 = Extreme Risk1.51 - 2.49 = Severe Risk2.5 - 3 = Moderate Risk*The risk score is calculated using a formula that considers a wide range of factors related to the assessed breach.
Exploit: Fraudelent email scam
St Ambrose Catholic Parish: Local Catholic Parish based in Brunswick, Ohio
 | Risk to Small Business: 2.444 = Severe: Bad actors sent fraudulent emails on behalf of a construction company that was contracted to complete work on the church building. The emails claimed that the parish was two months behind on project payments and included instructions for wiring payment to an external bank account. To execute the fraud, hackers first gained access to the email accounts for the construction company, extending the cybersecurity event beyond just the church. |
 | Individual Risk: 3 = Moderate: There is no indication that any personal information was compromised in this breach. |
How it Could Affect Your Customers’ Business: As this episode demonstrates, email scams can be a convincing way to execute fraud, and companies need to educate their employees about the signs of deception while also equipping them with training in best practices to avoid being a victim of a cybercrime. Unfortunately, events like this are incredibly commonplace and can happen to anyone, but companies are still responsible for protecting their systems.
ID Agent to the Rescue: BullPhish ID simulates phishing attacks and conducts security awareness training campaigns to educate your employees, making them the best defense against cybercrime. Click the link to get started: https://www.idagent.com/bullphish-id
Risk Levels:1 - 1.5 = Extreme Risk1.51 - 2.49 = Severe Risk2.5 - 3 = Moderate Risk*The risk score is calculated using a formula that considers a wide range of factors related to the assessed breach.
Exploit: Ransomware
CityComp: Germany-based enterprise IT service provider
 | Risk to Small Business: 1.888 = Severe Unlike most ransomware attacks that encrypt a company’s files and render them unavailable until a payment is made, this incident was a more unique form of blackmail. Hackers demanded $5,000 and promised to upload stolen client data if their request wasn’t met on time. In the meantime, they published a portion of the data on the Dark Web. Although most of the compromised data released thus far has been focused on contact information, meeting notes, and IT specifications, it can still be used to proliferate future attacks that involve more sensitive personal information. |
 | Individual Risk: 1.777 = Severe: Hackers stole 526 GB of the company’s client records including financial and private information. In total, more than 300,000 files were exposed during the breach. Although this information seems mostly technically-oriented, it’s always problematic when personal information is published on the Dark Web. |
Customers Impacted: Unknown
How it Could Affect Your Customers’ Business: Across the board, ransomware attacks are on the rise, and this episode is a reminder that they are becoming more complicated as well. Not only do companies need to have a robust defense system to prevent these incidents from occurring in the first place, but they need the tools to know what happens to company data and client information if it is unleashed on the Dark Web.
ID Agent to the Rescue: Dark Web ID can find out how payment data is used on the Dark Web, even in the case of a malware attack. We work with MSPs to strengthen their security suite by offering industry-leading detection. Find out more here: https://www.idagent.com/dark-web/
How it Could Affect Your Customers’ Business: Across the board, ransomware attacks are on the rise, and this episode is a reminder that they are becoming more complicated as well. Not only do companies need to have a robust defense system to prevent these incidents from occurring in the first place, but they need the tools to know what happens to company data and client information if it is unleashed on the Dark Web.
ID Agent to the Rescue: Dark Web ID can find out how payment data is used on the Dark Web, even in the case of a malware attack. We work with MSPs to strengthen their security suite by offering industry-leading detection. Find out more here: https://www.idagent.com/dark-web/
1 - 1.5 = Extreme Risk1.51 - 2.49 = Severe Risk2.5 - 3 = Moderate Risk*The risk score is calculated using a formula that considers a wide range of factors related to the assessed breach.
Exploit: Computer virus
Porr: Construction company serving as the largest domestic building contractor in Vienna
 | Risk to Small Business: 2.222 = Severe: A computer virus temporarily disabled the company’s phone and email service. Although no sensitive data was accessed during the network outage, communication channels were taken entirely offline, and the search for a solution is still ongoing. |
 | Individual Risk: 2.571 = Moderate: According to an official statement from the company, no company data was at risk, and individual information was not compromised in the cyberattack. |
Customers Impacted: Unknown
How it Could Affect Your Customers’ Business: It remains unclear how this virus entered the company’s infrastructure, which signals the need for every organization to understand its vulnerabilities and prepare for the worst. Fortunately, sensitive information wasn’t compromised, but a high-profile breach that disables communication infrastructure can have far-reaching consequences for any small business.
ID Agent to the Rescue: With BullPhish ID, MSPs can provide a more complete picture of a company’s security posture and potential risk, transforming the weakest links of an organization into their strongest points of protection. Find out how you can get started with us here: https://www.idagent.com/bullphish-id
How it Could Affect Your Customers’ Business: It remains unclear how this virus entered the company’s infrastructure, which signals the need for every organization to understand its vulnerabilities and prepare for the worst. Fortunately, sensitive information wasn’t compromised, but a high-profile breach that disables communication infrastructure can have far-reaching consequences for any small business.
ID Agent to the Rescue: With BullPhish ID, MSPs can provide a more complete picture of a company’s security posture and potential risk, transforming the weakest links of an organization into their strongest points of protection. Find out how you can get started with us here: https://www.idagent.com/bullphish-id
Risk Levels:1 - 1.5 = Extreme Risk1.51 - 2.49 = Severe Risk2.5 - 3 = Moderate Risk*The risk score is calculated using a formula that considers a wide range of factors related to the assessed breach.
Exploit: Ransomware
Power Distribution Company of Telangana: Electricity distribution business
 |
Risk to Small Business: 2.111 = Severe: Ransomware brought down the IT systems of the Power Distribution Company of Telangana when an employee inadvertently clicked on an email containing malicious software. Once the virus was unleashed, it was able to rapidly compromise the entire network. Although the utility’s network is down, the power supply was not disrupted.
|
 | Individual Risk: 3 = Moderate: There is no indication that personal data was compromised as part of the breach. |
Customers Impacted: To be determined
How it Could Affect Your Customers’ Business: Any time critical utilities are impacted by a data breach, it’s a reminder that the importance of cybersecurity extends just beyond technological capabilities. As ransomware attacks are on the rise, companies should evaluate their threat landscape while developing plans to quickly and effectively restore operations.
ID Agent to the Rescue: Designed to protect against human error, Bullphish ID simulates phishing attacks and manages security awareness training campaigns to educate employees, making them the best defense against cybercrime. Learn more here: https://www.idagent.com/bullphish-id.
How it Could Affect Your Customers’ Business: Any time critical utilities are impacted by a data breach, it’s a reminder that the importance of cybersecurity extends just beyond technological capabilities. As ransomware attacks are on the rise, companies should evaluate their threat landscape while developing plans to quickly and effectively restore operations.
ID Agent to the Rescue: Designed to protect against human error, Bullphish ID simulates phishing attacks and manages security awareness training campaigns to educate employees, making them the best defense against cybercrime. Learn more here: https://www.idagent.com/bullphish-id.
Risk Levels:1 - 1.5 = Extreme Risk1.51 - 2.49 = Severe Risk2.5 - 3 = Moderate Risk*The risk score is calculated using a formula that considers a wide range of factors related to the assessed breach.Bit by bit helps client networks run smooth and secure.. visit our website at www.bitxbit.com


No comments:
Post a Comment